The Purpose of our TSI Password Manager is simplifying security and data access. It works in the real world as a reliable trusted platform module making data processes secure.
-
What is the purpose of a password manager?
-
What are the advantages for my team?
This document answers these two questions and helps uses awash in passwords get started.
![]()
- A password manager is a technology that allows people to securely preserve strong passwords. It lets us create and manage many passwords for our computers and online services. Think of it as a locket for your knowledge keep safes. A safe is a vault that protects one’s valuables.
- The advantages are: Using proven effective technologies to protect preserve and enhance computer systems. Password managers have been around for a long time. They help generate highly randomized well formulated complex passwords. Storing them in an encrypted database, offsite adds a layer of protection. Passwords can be securely accessed as need arises.
Passwords are a fact of life.
Going back to the dark ages, passwords were necessary to entry to the castle. Inside people’s livelihood was secure, protected and preserved. In the tech world, dipping into recent history “the first passwords were simple and easily stored, since sophisticated hacking [and] networks [and not to mention] password-cracking programs did not yet exist. But the system was also easily duped. In 1962, Allan Scherr, a Ph.D. researcher with access to CTSS, printed out all of the passwords stored in the computer, so he could use CTSS for more than his four-hours-per-week allotment.” https://mashable.com/2013/12/30/history-of-the-password/
Dr. Scherr was hacking a written list usernames and passwords {still easy to lists dot computer monitors in many offices} to gain time at a punch card interface he went on masquerading as others he went on to a prominent career at IBM and other noted companies retiring in 2001 as senior vice president of software engineering for EMC Corporation. Allan L. Scherr – Wikipedia. In 2001 of course there was no HAL like computer interface or bases on the moon but hackers were search for list. In fact: in 1999 there was a renaissance of sorts in hacking with the release of Windows 98. “In the wake of Microsoft’s Windows 98 release, 1999 becomes a banner year for security (and hacking).” CNN.com – Timeline: A 40-year history of hacking – November 19, 2001 An entire new industry was born. New software vendors and product manufactures to keep pace with actors that looked for ways to compromise user’s systems.
The players have not gone away, the good ones or the bad ones are firmly rooted. At the base of their attack vectors are passwords. If you use digital tools and connect to the internet, you’re vulnerable to cybercrime. It doesn’t matter the size, sector, or location of your business. With so many passwords, having the one we need, when we need it is critical TSI Password Manager is the solutions.
As a trusted IT services provider, TSI is committed to doing everything we can to keep the bad guys from getting into your network: we set up firewalls, detect and block malware, patch servers and systems, and a lot more. But even the best protections can be foiled if a hacker gets their hands on passwords. The are still the key as they were in Scherr’s day to access access systems and data — and for small- and medium sized businesses (SMBs), the financial consequences of a data breach can be devastating.
1 “2019 Data Breach Investigations Report,” Verizon. https://enterprise.verizon.com/resources/reports/dbir/ (Accessed October 2019).
2 “2019 Cost of a Data Breach Report,” IBM, Ponemon Institute. https://www.ibm.com/security/data-breach (Accessed October 2019).

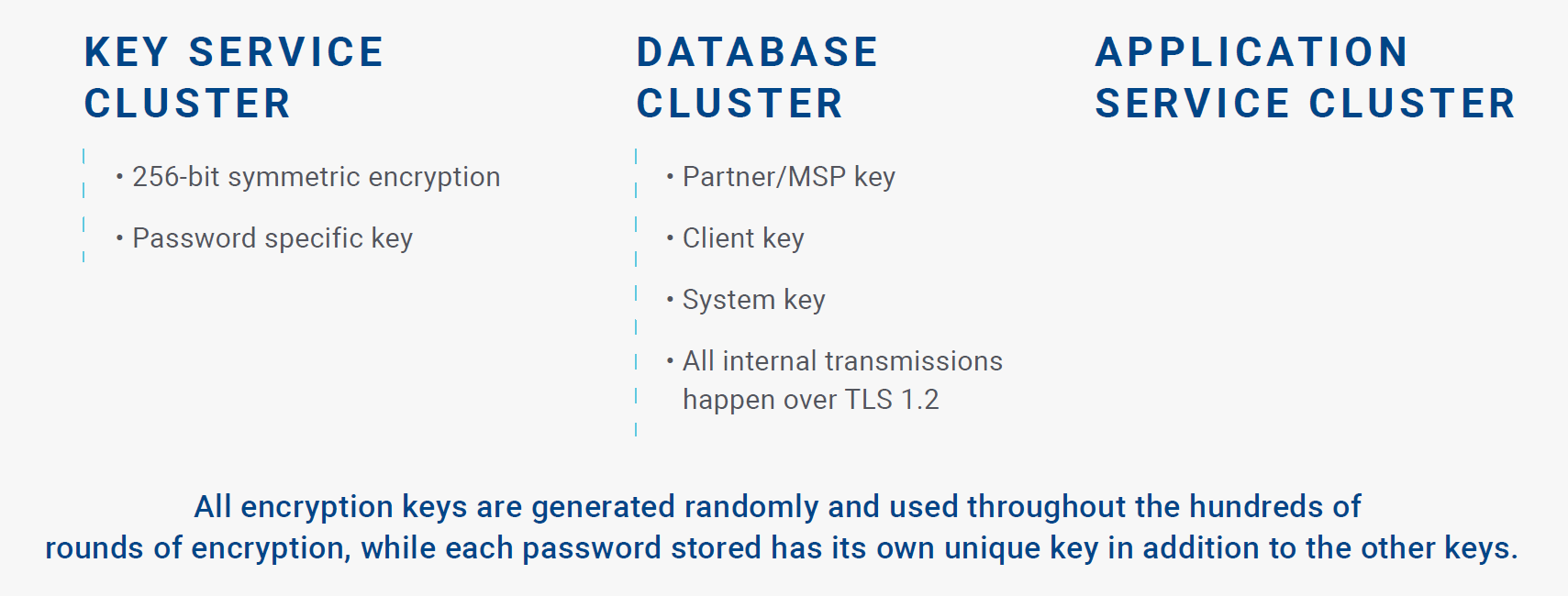
TSI Password Manager secures your new password records are input to the internet browser on your computer. From there they are protected in transit by 2048-bit RSA keys, and at rest using over 300 different rounds of 256-bit symmetric encryption, with six different randomly generated keys. Your unique encryption key (organization key) is the final step in unencrypting your data for view within the browser.
Easy as 1,2,3.
Security problem or need system support?
If you have:
- a security problem,
- technology question,
- configuration issue,
- had a network intrusion, malware or
- item place in quarantine,
call the Tekuser Service Desk at (336) 373-110(5).
Or submit a request by clicking the get help button below.

ORGANIZATION KEY
Two of the encryption keys used are unique to each password record, and one of the encryption keys called the Organization key is created and stored only on the server side. This encryption key is never stored or maintained anywhere except within the TSI Password Manager infrastructure.

PASSWORD AND
PASSPHRASE TRANSMISSION
All inbound and outbound data communication traffic with the TSI Password Management happens over TLS
1.2 using 2048-bit RSA keys to ensure the protection of your data in transit.

WEB APPLICATION FIREWALL PROXY
Unique encryption keys are retrieved from numerous sources for each password.