Ads are exploit gateways
Ads are exploit gateways. Most ads convey a product promotion or endorse someone or something. Frequently the browser based kind are used as data collectors used to invade ones privacy. The worst kind of ads called malvertising are not legitimate ads but a con to get...
Net nuetrality is necessary
Net neutrality is necessary for our privacy. This article encourages taking action now to let your Congressperson know that you care and are aware. If you are in the sixth district of North Carolina Mark Walker’s Greensboro office info is at the bottom of the...
Internet of things
The internet of things is very exciting. Enjoy the excitement. It is amazing. A few years ago, a friend had an exciting idea. It was on the edge of the internet of things. Diana came to me because she remembered our talking about a simple electronic device called a...Keeping systems up-to-date is critical
Keeping systems up-to-date is a critical piece in the computer security puzzle. More than making sense from a security perspective keeping systems to update is a good practice because it is more of a roll-out of new features and functions. With the latest versions of...Sites Infected with CryptXXX Ransomware
Sites Infected with CryptXXX Ransom-ware Over 2,000 WordPress – and Joomla-Based are known to be infected. According to Trend Micro most sites infected with CrptXXX Ransom-ware are aimed primarily at US users followed by France and Japan. Sites infected with...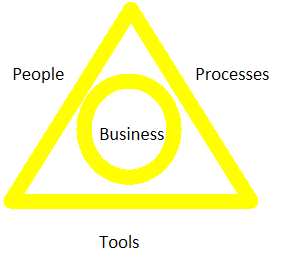
Customer Management
Customer Management is all about how your prospects feel about your offering. The best way to get them to the emotion they want is to get back to the basics: Understanding the three critical elements in everything we do – People, Process, Tools. It is the coffee you...