
by Dan | Jul 6, 2021 | Clouds, Data Backup and restore, IT Blueprint, Password Manager, Security, Technology, Training
Businesses, organizations, and individuals need to have an anti-phishing strategy. Just this simple step is minimizing the risk of successful phishing attacks. Staying safe from phishing attacks is a practice. Putting this handbook into your policies and procedures...

by David Mengert | Mar 13, 2021 | Password Manager, Security, Training
An alert pops up on your computer: It’s time to change your password again. Sigh. Fine. You’ll just change from password4! to password5! and— Not so fast. Regular password changes are meant to make sure that even if someone gets your login credentials, they won’t be...

by David Mengert | Jan 7, 2021 | Clouds, Data Backup and restore, Privacy, Security, Training
To celebrate data Privacy Day Tekmar is offering a month of help desk support as a bonus add-on with 60 day subscription for our TSI Password manager. The Purpose of TSI Password Manager is simplifying password management for businesses and users. What is the purpose...

by Dan | Oct 18, 2019 | Security, Technology, Training
Malware and ransomware Prevention Steps Avoiding malware and ransomware prevention steps ate simple actions we can all take to avoid exploits and file-encryption exploits. THese steps are not exhaustive or exhausting for our users. They do help. Sign up for our...

by David Mengert | Aug 18, 2018 | Clouds, Desktop Apps, IT Blueprint, MSO 365, Privacy, Security, Technology, Training
How to move your email safely securely for free, to a new provider. This article explains how to move your your email to a new host (provider). We begin by describing the situation and then discuss the four steps to migration. Lastly, we conclude by summarizing the...
by David Mengert | Jun 19, 2018 | Clouds, Desktop Apps, IT Blueprint, Technology, Training
Watch IT Assess IT Update IT Secure IT Is the model Tekmar Solution, Inc. uses as managed service provider. The four step process helps blending the best technologies for users, customers and the entire global computing environment. Our models stay steady for the...
by Dan | May 9, 2017 | Clouds, MSO 365, Technology, Training
Another Great One Drive feature has been updated. The Vision office 365 from its earliest days was a consistently growing and adapting set of forms that helped users stay in front of demands. The vision is pretty true. The great feature of cc’ing a user when a...
by David Mengert | Apr 25, 2017 | Security, Technology, Training, Web presence
Technology and a golden ticket at Black Mountain Chocolate Factory For Easter, I used technology and a golden ticket to have a great time with my youngest daughter. The golden ticket came from the Black Mountain Chocolate Factory in downtown Winston Salem. It’s only...
by David Mengert | Apr 19, 2017 | Clouds, Privacy, Security, Technology, Training, Web presence
Ads are exploit gateways. Most ads convey a product promotion or endorse someone or something. Frequently the browser based kind are used as data collectors used to invade ones privacy. The worst kind of ads called malvertising are not legitimate ads but a con to get...
by David Mengert | Apr 16, 2017 | Clouds, Privacy, Security, Training
Managing critical systems Managing critical sytsems is a huge concern for big business and governments. Despite the media frenzy over the NSA data release about potential Microsoft exploits, this data is widely known among hackers and IT professionals. Many owners and...

by David Mengert | Apr 8, 2017 | Anthropology, Technology, Training
Coffee shops replace shopping malls as a social destination. Some of my thinking in this regard derives from popular TV cultural. The representations that people saw in Frazier’s Cafe Nervosa and Central Perk where Friends went for a forum can be denied. photo...
by David Mengert | Apr 1, 2017 | Privacy, Security, Technology, Training
A thin majority in the US House voted to repeal broadband privacy. They decided yesterday to give our personal information away. President Donald Trump now stands between you and your browsing privacy. The vote broke along party lines, with most Republicans voting...

by David Mengert | Mar 28, 2017 | Anthropology, Privacy, Security, Technology, Training, Web presence
Net neutrality is necessary for our privacy. This article encourages taking action now to let your Congressperson know that you care and are aware. If you are in the sixth district of North Carolina Mark Walker’s Greensboro office info is at the bottom of the...
by David Mengert | Mar 25, 2017 | Anthropology, Security, Technology, Training
Loving kindness meditation May I be safe and protected from inner and outer harm. May I be happy and contented. May I be healthy and whole to whatever degree possible. May I experience the ease of well being – loving kindness meditation The posting of the...

by David Mengert | Feb 24, 2017 | Desktop Apps, Privacy, Security, Technology, Training
Microsoft privacy awareness is and has been on the forefront of concern as long as I have been in tech. That is 25 years. What to do about this real concern. Awareness in the first step. A coworker prompted me about it last month. Many of the people we see every have...

by David Mengert | Feb 21, 2017 | Technology, Training
Getting my standing desk back in place after 7 months in a seat is a good. What a relief. When I started the standing desk, I was using cases to elevate the monitors and it really worked. Tekmar got really busy at the end of the April, fighting cybercrime and covering...

by David Mengert | Feb 3, 2017 | Desktop Apps, Technology, Training
5 reasons business class laptops are better The first laptop in my hands was in the early 1990s. It was a business class machine made by Tandy corporation. That’s right Tandy! The parent company of the once thriving consumer electronics retailer, Radio Shack. Tandy...

by Dan | Jan 21, 2017 | MSO 365, Technology, Training
Calling slow upgrade Office 2013 users: Calling slow upgrade Office 2013 users: Beginning March 1, 2017, your users will no longer see Office 2013 as an option for download through the Office 365 portal, and admins will no longer have the option under Software...
by Dan | Dec 29, 2016 | Clouds, Desktop Apps, IT Blueprint, Security, Technology, Training
This post details why training people to watch for danger signs is a great start and important to information security. It offers several tips and tricks to make it easier for home and business users. Training is not enough it’s a mindful approach that makes the...
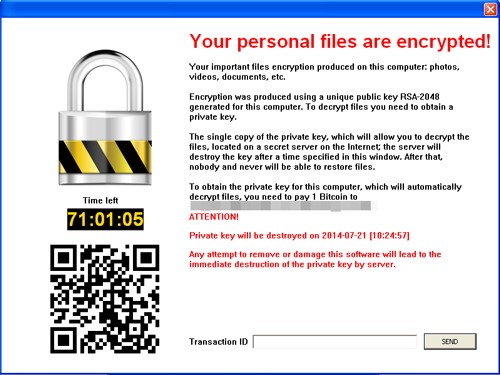
by Dan | Mar 22, 2016 | Security, Technology, Training
Although it is the last item on the Legal Tech News Nine Steps to Fight Crypto Locker, this rapidly changing exploit needs more attention…Cryptolocker Malware prevention requires awareness. Training everybody you know and work with is the answer. “Security...















