
by David Mengert | Aug 18, 2018 | Clouds, Desktop Apps, IT Blueprint, MSO 365, Privacy, Security, Technology, Training
How to move your email safely securely for free, to a new provider. This article explains how to move your your email to a new host (provider). We begin by describing the situation and then discuss the four steps to migration. Lastly, we conclude by summarizing the...
by David Mengert | Apr 25, 2017 | Security, Technology, Training, Web presence
Technology and a golden ticket at Black Mountain Chocolate Factory For Easter, I used technology and a golden ticket to have a great time with my youngest daughter. The golden ticket came from the Black Mountain Chocolate Factory in downtown Winston Salem. It’s only...
by David Mengert | Apr 19, 2017 | Clouds, Privacy, Security, Technology, Training, Web presence
Ads are exploit gateways. Most ads convey a product promotion or endorse someone or something. Frequently the browser based kind are used as data collectors used to invade ones privacy. The worst kind of ads called malvertising are not legitimate ads but a con to get...
by David Mengert | Apr 16, 2017 | Clouds, Privacy, Security, Training
Managing critical systems Managing critical sytsems is a huge concern for big business and governments. Despite the media frenzy over the NSA data release about potential Microsoft exploits, this data is widely known among hackers and IT professionals. Many owners and...
by David Mengert | Apr 1, 2017 | Privacy, Security, Technology, Training
A thin majority in the US House voted to repeal broadband privacy. They decided yesterday to give our personal information away. President Donald Trump now stands between you and your browsing privacy. The vote broke along party lines, with most Republicans voting...

by David Mengert | Mar 28, 2017 | Anthropology, Privacy, Security, Technology, Training, Web presence
Net neutrality is necessary for our privacy. This article encourages taking action now to let your Congressperson know that you care and are aware. If you are in the sixth district of North Carolina Mark Walker’s Greensboro office info is at the bottom of the...
by David Mengert | Mar 25, 2017 | Anthropology, Security, Technology, Training
Loving kindness meditation May I be safe and protected from inner and outer harm. May I be happy and contented. May I be healthy and whole to whatever degree possible. May I experience the ease of well being – loving kindness meditation The posting of the...

by David Mengert | Feb 24, 2017 | Desktop Apps, Privacy, Security, Technology, Training
Microsoft privacy awareness is and has been on the forefront of concern as long as I have been in tech. That is 25 years. What to do about this real concern. Awareness in the first step. A coworker prompted me about it last month. Many of the people we see every have...
by David Mengert | Feb 6, 2017 | Clouds, Security, Technology, Web presence
The internet of things is very exciting. Enjoy the excitement. It is amazing. A few years ago, a friend had an exciting idea. It was on the edge of the internet of things. Diana came to me because she remembered our talking about a simple electronic device called a...
by Dan | Jan 28, 2017 | Clouds, Security, Technology, Web presence
Keeping systems up-to-date is a critical piece in the computer security puzzle. More than making sense from a security perspective keeping systems to update is a good practice because it is more of a roll-out of new features and functions. With the latest versions of...
by Dan | Dec 29, 2016 | Clouds, Desktop Apps, IT Blueprint, Security, Technology, Training
This post details why training people to watch for danger signs is a great start and important to information security. It offers several tips and tricks to make it easier for home and business users. Training is not enough it’s a mindful approach that makes the...

by David Mengert | Dec 21, 2016 | Clouds, MSO 365, Security, Technology
Bye bye Firefox security first: Many admins Tekmar Solutions works with swear by the Firefox Browser. We like it too. But rarely use it with Office 365 or other transaction oriented situations. Admins will have to say bye bye to Firefox secure first effective in March...
by David Mengert | Apr 18, 2016 | Desktop Apps, Privacy, Security, Technology
Now is the time to upgrade, Apple end supportfor QuickTime for Windows. They are no longer going to keep Windows QuickTime users, keeping them secure in not profitable. Keeping your software and systems updated and running smoothly is profitable, business critical. If...
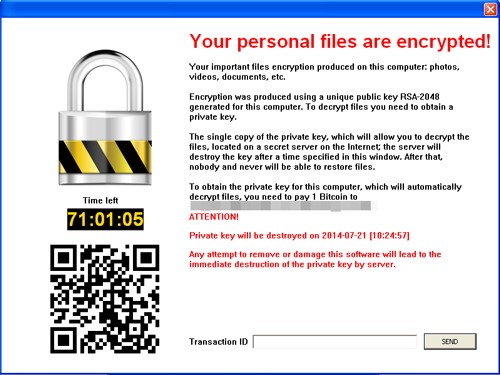
by Dan | Mar 22, 2016 | Security, Technology, Training
Although it is the last item on the Legal Tech News Nine Steps to Fight Crypto Locker, this rapidly changing exploit needs more attention…Cryptolocker Malware prevention requires awareness. Training everybody you know and work with is the answer. “Security...
by David Mengert | Dec 9, 2015 | Security, Technology
One of our customers found themselves proud owners of some new- technology from Time Warner Business Class. We got the call yesterday because although they are paying for cable internet service, it didn’t include wireless. So we installed a used 450 Mbps Wireless...

by David Mengert | Apr 2, 2015 | Clouds, Security, Technology
Phishing scams 2015 on the rise ahead of April 15 The IRS warned at the beginning of the year that they expected an onslaught of malware and targeted phishing scams 2015. As the tax filing deadline for Businesses came and went in mid march the attacks...

by Dan | Mar 15, 2015 | Clouds, Desktop Apps, IT Blueprint, Security, Technology
5 easy steps to reduce info security risks are really as easy, and many people and companies are taking them up today. User training is the most important and easiest key to a better info-security profile for businesses. Most of the big corporations and even large...

by Dan | Feb 23, 2015 | Clouds, Security, Technology
“One many pronged advantage of open source software like WordPress is monitoring and alertness that sponsors put into protecting the community. Update @9:45PM PST: About an hour before posting this we alerted the official WP repository admins about this issue....
by Dan | Feb 21, 2015 | Security, Technology
Superfish Lenovo spears their customers. Although Lenovo apparently knew about the problems with this potentially unwanted programs, PUP, that turned out to be really bad, they did not notify customers until the story was broken by Marc Rogers on February 19. When are...

by Dan | Feb 17, 2015 | Security, Technology, Training
Net Neutrality needs you to comment now so that giant Telecom does not have the right to control the net. This page previously contain a widget from Fight For the Future posted on the internet that helped one call their Senators and Representative. That was back in...














