by Dan | Apr 8, 2015 | Clouds
Sky watching event Although Tekmar is in the clouds business, we hope there none in the way of this event. Technology clouds never get in the way of sky watching events. Learn more about cloud computing… If you look up you might see 10 to 20 meteors per hour at...

by David Mengert | Apr 2, 2015 | Clouds, Security, Technology
Phishing scams 2015 on the rise ahead of April 15 The IRS warned at the beginning of the year that they expected an onslaught of malware and targeted phishing scams 2015. As the tax filing deadline for Businesses came and went in mid march the attacks...

by Dan | Mar 15, 2015 | Clouds, Desktop Apps, IT Blueprint, Security, Technology
5 easy steps to reduce info security risks are really as easy, and many people and companies are taking them up today. User training is the most important and easiest key to a better info-security profile for businesses. Most of the big corporations and even large...
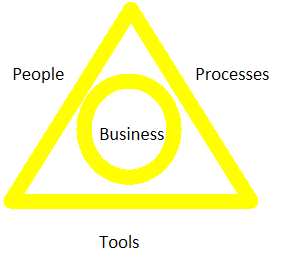
by David Mengert | Feb 24, 2015 | Clouds, IT Blueprint, Technology, Web presence
Customer Management is all about how your prospects feel about your offering. The best way to get them to the emotion they want is to get back to the basics: Understanding the three critical elements in everything we do – People, Process, Tools. It is the coffee you...

by Dan | Feb 23, 2015 | Clouds, Security, Technology
“One many pronged advantage of open source software like WordPress is monitoring and alertness that sponsors put into protecting the community. Update @9:45PM PST: About an hour before posting this we alerted the official WP repository admins about this issue....
by Dan | Feb 20, 2015 | Clouds, IT Blueprint, MSO 365, Technology
Email is a great tool, but it’s a huge distraction in itself. I try to not look at it till after 9:30 every day. Then I follow the same process: go through the newest emails, deal with the priority and delete them. Flag the ones that have to be dealt with by end of...

by David Mengert | Feb 2, 2015 | Clouds, IT Blueprint, Security, Technology, Training
Three simple steps prevent delivering breakthrough experiences for the bad guys. The choice is yours whether to take action or not.. “For the third time in the last couple of weeks, Adobe is dealing with a zero day vulnerability in Flash. The company is working...

by Dan | Oct 14, 2014 | Clouds, Desktop Apps, IT Blueprint, MSO 365, Security, Technology
Three simple reasons that upgrading makes sense now: Always The has been huge growth in data over the past few years. Big data this and big data that. Where do we put it and what do we do with it? We actually have plenty of places to put it all… 16k is how many...
by Dan | Sep 12, 2014 | Clouds, IT Blueprint
3 Key Answers to Security Concerns The 3 key answers to security concerns are right under our noses. What makes a business successful is the same set of concerns as what keeps its data safe. Companies are people, processes and hard system, technology. They must...
by David Mengert | Sep 11, 2014 | Clouds, IT Blueprint, Technology
Internet Slow Down Day Internet slow down day came and went without inflicting any real slowdown on network traffic. The echoing halls of government had more traffic than usual yesterday. Phones were ringing and email boxes brimming with comments on the idea that...
by Dan | Sep 10, 2014 | Clouds, Technology
The industry lobby is dismissive and deceptive. Its anti-government no-regulation appeal adds confusion to an already complicated situation. The Industry giants have pulled together under the umbrella of trade associations and powerful business lobbying groups. They...
by David Mengert | Sep 4, 2014 | Clouds, Security, Technology
Home Depot Breach Today’s Home Depot breach is another in the series of cracks that show up weekly in companies security portfolios. Information that I received this morning, Home Depot did the right thing and came clean about the breach. Big corporations, the US...
by Dan | Sep 3, 2014 | Clouds, Desktop Apps, IT Blueprint, Security, Technology
Windows 8.1 Pro Opportunity Tuesday 8/9 The Windows 8.1 pro opportunity is easy for people. Many of our clients have taken the opportunity and are enjoying the benefits of easier work desktop, secure transparency to other devices. “Do you ever use your PC for work?”...
by David Mengert | Aug 16, 2014 | Clouds, Security, Technology, Training
All internet users should beware when updating their systems. Business people should push back against busy work. Busy work is the part of business that makes more work but does not get you nearer to your goals. All kinds of busy work are a drain on good energy needed...
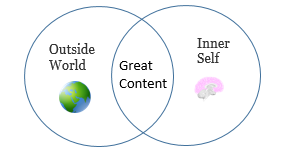
by David Mengert | Aug 12, 2014 | Clouds, Security, Technology, Web presence
Great content: What that means This man is not Weird Al’s Father In July on a simple mission – find a better language resource I searched many sights. There are millions of good blogs and web sites. Most have genuinely fine information and stories that have an...
by David Mengert | Jul 30, 2014 | Clouds, Security, Technology
Net Neutrality EFF to FCC: Defend the Neutral Internet: Agency Must Abandon Dangerous Traffic-Discrimination Plan The Internet is a network of networks. People often talk about it as the cloud today, but that is a marketing term. It is the same Net we businesses and...
by David Mengert | Jul 12, 2014 | Clouds, IT Blueprint, Security, Technology
The anti-Microsoft attitude is curious. The Mac PC war rages on even though both are less dominant brands than they recently were. The anti-Microsoft approach is especially interesting when expressed by people and companies whose practices are built around PCs and...
by David Mengert | Jun 29, 2014 | Clouds, Desktop Apps, MSO 365, Technology
PST File Hell Make Missing email a thing of the past… The problems with holding on to the old instead of going through the learning curve are many. The most frustrating is that we tend to get caught repeating the problems of yesterday. Missing emails...
by David Mengert | Jun 20, 2014 | Clouds, Technology, Training, Web presence
Things to know about a new initiative Google is launching this week called: “Made with Code.” WHAT IS “MADE WITH CODE?” The Google-led version of this initiative is getting a lot of coverage in the national press. It’s an effort to get...
by David Mengert | Jun 19, 2014 | Clouds, Desktop Apps, IT Blueprint, Security, Uncategorized
Another New malware exploit spreading calls for renewed vigilance. A new malware exploit spreading the Zeus Trojan via phishing messages is at work on the internet. It was discovered by researchers early Wednesday. People launching these malware and viruses are...








