by Dan | Jul 13, 2021 | Security, Technology
Reported in the New York Times today, by David Sanger, the aggressive ransomware organized crime syndicate believed base in Russia has gone offline. He lists several possible gambits. My favorite ” a third is that REvil decided that the heat was too intense, and...

by Dan | Jul 8, 2021 | Security, Technology
Printnightmare has kept IT and systems staff alerted for the past week. It was originally attributed to: An accidental leak Leaking the details for this vulnerability happened by accident, out of a confusion with another issue, CVE-2021-1675, also impacting Print...

by Dan | Jul 6, 2021 | Clouds, Data Backup and restore, IT Blueprint, Password Manager, Security, Technology, Training
Businesses, organizations, and individuals need to have an anti-phishing strategy. Just this simple step is minimizing the risk of successful phishing attacks. Staying safe from phishing attacks is a practice. Putting this handbook into your policies and procedures...

by Dan | Feb 13, 2021 | Password Manager, Security
If you use the same password for multiple systems—online shopping, email, your company’s cloud bookkeeping solution, etc.—you are not alone. The best password is unique, yet even Facebook founder Mark Zuckerburg did that. And in 2016 his LinkedIn credentials were...

by Dan | Apr 5, 2020 | MSO 365, Technology, Tekmar Time Machine
Tekmar Started Moving …Clients away from antiquated systems in 2012 and completed the migration to Office 365 in couple years. Here in an article from the time machine. <Note some links may not work.> <strong>Microsoft office 2003 and Windows...

by Dan | Oct 18, 2019 | Security, Technology, Training
Malware and ransomware Prevention Steps Avoiding malware and ransomware prevention steps ate simple actions we can all take to avoid exploits and file-encryption exploits. THese steps are not exhaustive or exhausting for our users. They do help. Sign up for our...
by Dan | Feb 20, 2019 | Uncategorized
[wps_products]
by Dan | May 9, 2017 | Clouds, MSO 365, Technology, Training
Another Great One Drive feature has been updated. The Vision office 365 from its earliest days was a consistently growing and adapting set of forms that helped users stay in front of demands. The vision is pretty true. The great feature of cc’ing a user when a...

by Dan | Feb 28, 2017 | Technology
AWS Amazon’s web servers down at the time this article was posted. AWS is part of a huge infrastructure that people rely on. It powers significant parts of our augmented-reality. My streaming music is down. Other people are affected in different ways. They’ll...
by Dan | Jan 28, 2017 | Clouds, Security, Technology, Web presence
Keeping systems up-to-date is a critical piece in the computer security puzzle. More than making sense from a security perspective keeping systems to update is a good practice because it is more of a roll-out of new features and functions. With the latest versions of...

by Dan | Jan 21, 2017 | MSO 365, Technology, Training
Calling slow upgrade Office 2013 users: Calling slow upgrade Office 2013 users: Beginning March 1, 2017, your users will no longer see Office 2013 as an option for download through the Office 365 portal, and admins will no longer have the option under Software...
by Dan | Dec 29, 2016 | Clouds, Desktop Apps, IT Blueprint, Security, Technology, Training
This post details why training people to watch for danger signs is a great start and important to information security. It offers several tips and tricks to make it easier for home and business users. Training is not enough it’s a mindful approach that makes the...
by Dan | Nov 16, 2016 | Technology, Web presence
Sites Infected with CryptXXX Ransom-ware Over 2,000 WordPress – and Joomla-Based are known to be infected. According to Trend Micro most sites infected with CrptXXX Ransom-ware are aimed primarily at US users followed by France and Japan. Sites infected with...
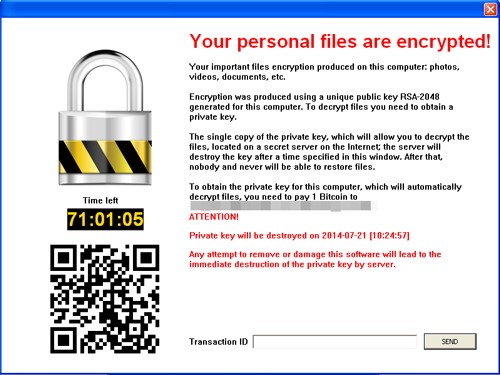
by Dan | Mar 22, 2016 | Security, Technology, Training
Although it is the last item on the Legal Tech News Nine Steps to Fight Crypto Locker, this rapidly changing exploit needs more attention…Cryptolocker Malware prevention requires awareness. Training everybody you know and work with is the answer. “Security...
by Dan | Apr 8, 2015 | Clouds
Sky watching event Although Tekmar is in the clouds business, we hope there none in the way of this event. Technology clouds never get in the way of sky watching events. Learn more about cloud computing… If you look up you might see 10 to 20 meteors per hour at...

by Dan | Mar 15, 2015 | Clouds, Desktop Apps, IT Blueprint, Security, Technology
5 easy steps to reduce info security risks are really as easy, and many people and companies are taking them up today. User training is the most important and easiest key to a better info-security profile for businesses. Most of the big corporations and even large...

by Dan | Feb 23, 2015 | Clouds, Security, Technology
“One many pronged advantage of open source software like WordPress is monitoring and alertness that sponsors put into protecting the community. Update @9:45PM PST: About an hour before posting this we alerted the official WP repository admins about this issue....
by Dan | Feb 21, 2015 | Security, Technology
Superfish Lenovo spears their customers. Although Lenovo apparently knew about the problems with this potentially unwanted programs, PUP, that turned out to be really bad, they did not notify customers until the story was broken by Marc Rogers on February 19. When are...
by Dan | Feb 20, 2015 | Clouds, IT Blueprint, MSO 365, Technology
Email is a great tool, but it’s a huge distraction in itself. I try to not look at it till after 9:30 every day. Then I follow the same process: go through the newest emails, deal with the priority and delete them. Flag the ones that have to be dealt with by end of...
by Dan | Feb 19, 2015 | Uncategorized
Microsoft Onenote, a strong point of Microsoft office, just got stronger. One Note is Microsoft’s click and write, draw and sketch, highlight and capture component. You don’t have to click save! Your Onenotes are auto-saved to secure cloud storage. If you...












